| | Tech Tips - Business IT Support Tips
Archive for 2012
Friday, October 12th, 2012
There are few things in life more frustrating than losing an android smartphone! That’s why the mobile security experts at Lookout have completely redesigned their Android application, with the most notable addition being the Signal Flare feature. This new feature Signal Flare automatically sends out signals via GPS, Wi-Fi, and wireless networks to Lookout’s servers whenever the phone battery gets low and is about to die. The data records the last known location of the phone, allowing users with the app installed to visit Lookout.com and see the last location their gadget was known to be located prior to it shutting down. This feature also offers a Scream Test that when selected sends out a loud alarm on a device on, even if your device is on silent, allowing you to locate your device if it is nearby.
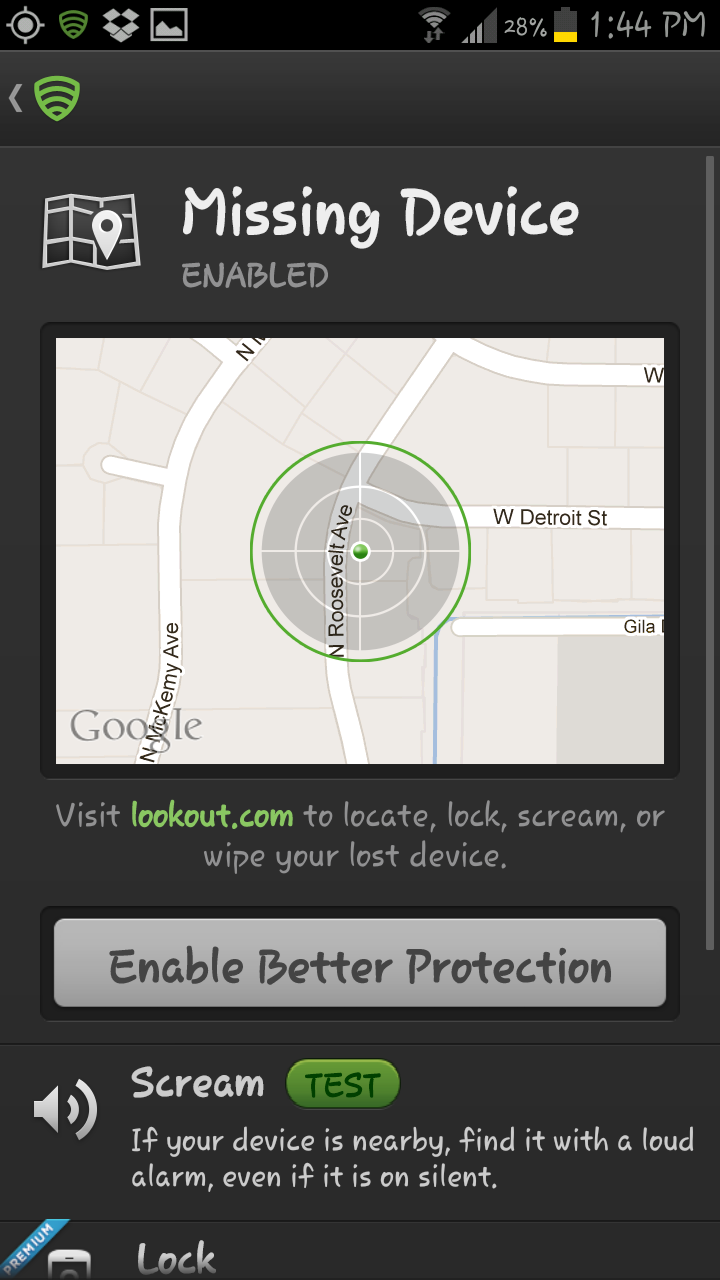
Signal Flare is just one of the many new cool features in the redesign of Lookout’s app. The redesign also includes a new Activity Feed that lists recent activity, such as app scans, data backup and even warnings of suspicious activity. There is also Safe Dialer, a feature that aims to prevent unwanted dialer attacks. This feature scans phone numbers before completing a call. Abheek Gupta, the product manager for the Lookout app, describes this feature as protection against a new kind of mobile malware referred to as dialer-based threats. It prevents malware from running up very high phone bills by automatically dialing premium-rate numbers or code based numbers that performs unauthorized actions.
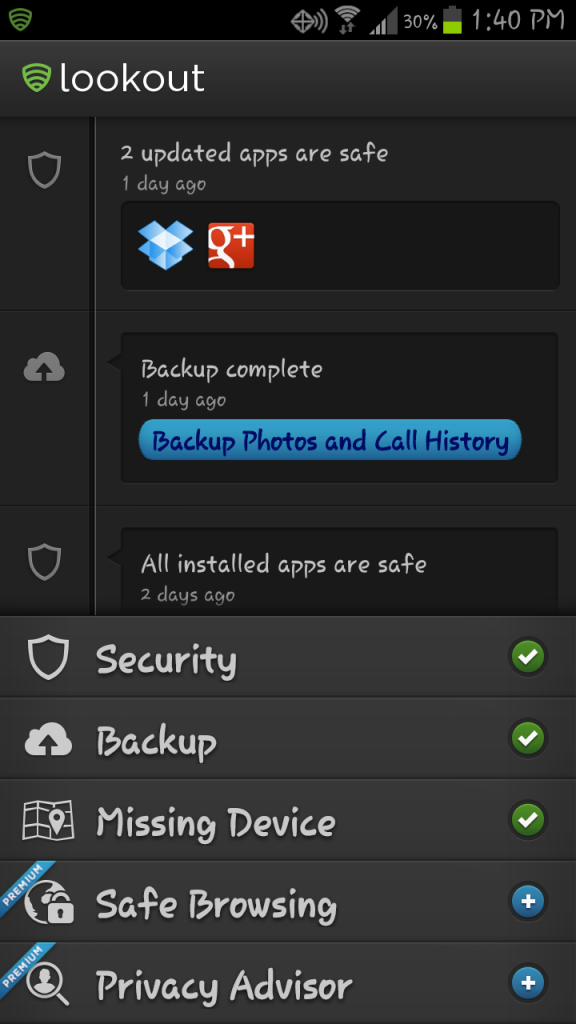
Launched over 3 years ago, Lookout has been downloaded by over 25 million people and offers both a free and paid version. Both the free and paid for version app perform a scan of all the apps on your phone to detect any database malware and security threats. The paid version offers extras such as additional web browsing, backup features, and privacy-protection.
According to Lookout, 30 percent of lost phones are not recovered due to a dead battery on the device. The ability to see your phone on a map at the last known location before the phone died should improve the odds of recovery. Keep in mind, Signal Flare does not log a device’s location if the phone is simply turned off. It will record the location of a device only when the low battery alert goes off, so this feature is probably not useful when it comes to trying to track down a phone thief. You can however, as long as the phone is still on, log into Lookout.com and send out a signal manually to locate your phone even if your device is not low on battery.
Do you already have Lookout Mobile Security app installed on your device? Make sure to update ASAP to get all of the great new features!
Tags: Android, app, application, cell phone, date backup, dead battery phone, dead cell phone, device, gadget, Lookout Mobile Security, losing phone, lost phone, missing phone, phone shutting down, safe dialer, signal flare, smartphone
Posted in my PC Techs News & Events | No Comments »
Tuesday, October 9th, 2012
Tablets and Smartphones can be a lot of fun for kids. There are plenty of games to play, websites to look at and apps to experiment with. These devices may also seem like convenient babysitters when you’re busy with work or chores. However, simply handing your mobile device over to your little ones poses several potential problems if you don’t take the time to child-proof it first.
Device Dangers
Giving the kids free reign of tablets or Android phones opens the door for them to access inappropriate web content, rack up accidental credit card charges and possibly even damage your device. Before letting your child play, it’s important to take precautions to ensure that both they and your Smartphone or Android tablet stay safe.
Always Monitor
The most obvious way to prevent youngsters from doing or seeing something they shouldn’t is to keep an eye on them. You never want to put your child in front of any electronic device without supervision, be it the television, the computer or your Android tablet. Monitoring your son or daughter’s activity lets you catch problems before they happen and gives you opportunities to teach them what is and isn’t acceptable when it comes to technology.
Keep Content Kid-Friendly
There’s a lot of content out there that you don’t want your children seeing. Fortunately there are many apps available to help you filter out anything objectionable. Mobicip is a kid-friendly browser that uses the same standards that schools do to filter out inappropriate web content. Norton Safety Minder lets you keep an eye on web activity as well as block certain sites. Other apps such as PlaySafe, Kids Place and ChildrenTV give you various tools to manage which apps, games and other content your children are allowed to access when they use your Samsung tablet or other device.
Lock Down Purchases
Accidental purchases, both of full apps and of items within apps, can result in credit card charges that you aren’t prepared for. iPhones include a setting that allows you to turn off in-app purchases, but currently the only way to prevent accidental charges on an Android phone is to block access to apps that may include them. The Famigo Sandbox app gives you a way to do this by allowing you to control which apps your youngsters use as well as minimizing access to other device functions such as text messaging.
Get a Protective Case
Whether it’s grippy or squishy, chunky or sleek, padded or gel-like, get a case for your device before handing it off to your child. Protection is more important than style. Little hands often lack coordination and are therefore more apt to drop things, including expensive electronics. Cases can even become part of the fun. Make your device look like a little person, wrap it in a high-density foam grip or nest it inside a squashy pillow. Whatever type of case you choose, you’ll know your Smartphone or Android tablet is safe and sound.
Before you let your little ones use your Android phone, Samsung tablet or other mobile device, make sure that you’ve taken the appropriate steps to make it safe. Cushion it with a case, install kid-friendly apps and keep an eye on your children as they play to ensure that they have a positive, fun experience.
Tags: child, child-proof phone, children, device dangers, electronic device, friendly content, fun, inappropriate web content, Kid friendly apps, kid-safe, kids, kids games online, monitor internet, safe browsing, smartphones, tablets, technology
Posted in Tech Club General | No Comments »
Thursday, October 4th, 2012
 Although I’ve been looking forward to “upgrading” my Android phone to a newer model, I’ve also been somewhat hesitant. I’ve known people who experienced nightmare scenarios when migrating to a new phone, encountering huge challenges during the transition that have kept them offline for days. When you depend on your phone to get your job done, the thought of being without it for any period of time can be scary. There are programs on the market designed to help you move your apps and data, but even with the assistance of an app it is easy for something to go wrong. Although I’ve been looking forward to “upgrading” my Android phone to a newer model, I’ve also been somewhat hesitant. I’ve known people who experienced nightmare scenarios when migrating to a new phone, encountering huge challenges during the transition that have kept them offline for days. When you depend on your phone to get your job done, the thought of being without it for any period of time can be scary. There are programs on the market designed to help you move your apps and data, but even with the assistance of an app it is easy for something to go wrong.
With a little preparation, it is possible to move to the new phone and minimize troubles. My goal is to help eliminate some of the worries you might have about transitioning to a new phone by sharing my recent experience.
The day when my new phone arrived, I took it out of the box and plugged it in to complete the charge on the battery. I figure by the time I’m ready, I’ll have a full charge on my new phone.
In the meantime, I looked at the installed applications on my old now old phone. I mostly used my home screens to first write down the names of the critical apps that were being used on a regular basis. My goal was to back up the settings and data for those apps so I could easily move them to the new phone. My list of critical apps included applications such as Car Expense tracking, Notetaking, Email, and Maps. Then there was a second list for the apps I use occasionally, which I made in order to determine if I could eliminate any apps that I no longer needed. Finally, I made a list of the apps I’ve paid for. I wanted to make sure I was able to get these applications activated on the new phone without any hassles.
It is crucial to know your email address, password and server connection settings if you have company or other email you access aside from Gmail. You’ll also want to make sure you have your Gmail account usernames and passwords before you continue. I went through the settings menu of my old phone and recorded the details for any accounts that I found listed. For any accounts that were shown, I double checked all of my notes to make sure I had to correct passwords. Of critical importance is the primary Google account registered on the phone. If you don’t know what the password is on this account you’ll want to try recovery methods before transitioning to the new phone.
Next, I wanted to get a complete backup of my data. The first thing I did was go through my critical apps and looked in the settings for each one to see if any had a built in export function, some of these apps did provide a way to export data from the app to a file on the SD card. Next, I wanted to backup my contacts. Most phones store contacts not only in Gmail and Hotmail, but also on the phone itself. To make sure I had all my contacts stored, I used the app Backup Assistant Plus to perform a backup of the local contacts on my phone.
I then took a USB cable and attached the cable to my phone and to a computer. With the old phone in data transfer mode, I was able to access the contents of the internal phone memory and the SD card from my computer. Via the USB connection from my PC I selected all of the files and folders from the phone’s memory and copied them to a temporary directory on my computer.
With a complete list of email accounts, passwords for apps, registration codes, and a backup of my contacts and data in hand I phoned Verizon to activate my new phone. Give yourself some time for this part since customer service can be a lengthy process. In my case, it took about half an hour on the phone with them before everything was finalized. The time of day you call will greatly determine your wait time for a representative to assist.
Finally, the new phone had been activated and restarted. At this point I successfully activated my Gmail using the same primary username and password as was used on the old phone. Next, after activation I launched to the desktop of my new phone and opened Google Play from the settings menu. Depending on your phone, you may see the same app named Android Market or Google Play. Here, you can select which Account to sync with. This is usually your primary Google account. You then select” My Apps” and then reveal “ALL”. This list has everything you’ve installed on your phone, including free and paid apps. It should now be possible to re-download and install apps that you previously paid for.
Once I re-installed all my paid apps, the final challenge was determining how to restore my data. I attached the new phone to my computer with a USB cable and placed it into the correct mode to communicate with my PC. Once again I could see drives mapped for my phone’s memory and SD card. This step required a little creativity because I had to determine on a case by case basis which apps I needed to migrate data for and how I could import the data to my phone. Once I identified what I needed to transfer, I copied over to the SD card on the new phone data from the temporary directory I made earlier. For apps that previously allowed me to export data on my old phone, I imported the data from within the app using the file that was created from the export operation.
My next step was to restore my contacts which I did using the features of Backup Assistant Pus. And finally, I double checked that my new phone and all apps on the phone were running the latest versions. While not the easiest process in the world, I was up and running in less than two hours. Not bad for a fast new phone with all of the same programs and features I’d come to enjoy.
So, don’t be fearful of getting that upgrade! If you find yourself needing to replace your next smart device it’s possible to do it yourself. Just be sure to take down as much information as you can and make a good backup copy of everything using several methods. Alternatively, if you would like help from someone experienced or would like someone to do it for you, please feel free to give me a call.
Tags: Android, android upgrade, app transfer, cell phone, contact transfer, data storage, data transfer, google play, how to transfer contacts, my pc techs, new phone, smart phone, transitioning phone
Posted in Tech Club General | No Comments »
Tuesday, September 11th, 2012
 GoDaddy, an Arizona web hosting company, experienced severe outages yesterday. The massive Distributed Denial of Service (DDoS) began late Monday morning, and the GoDaddy.com site itself went offline. Twitter user Anonymous Own3r, a member of the Anonymous hacktivist group, is claiming sole responsibility for the attack. According to the twitter account, Anonymous Own3r is an official member and security leader of the famous hacktavist group Anonymous, and claims the move is a reaction to the company’s support of the U.S. government’s efforts “to censor and control the Internet,” through its support of the Stop Online Privacy Act (SOPA). GoDaddy, an Arizona web hosting company, experienced severe outages yesterday. The massive Distributed Denial of Service (DDoS) began late Monday morning, and the GoDaddy.com site itself went offline. Twitter user Anonymous Own3r, a member of the Anonymous hacktivist group, is claiming sole responsibility for the attack. According to the twitter account, Anonymous Own3r is an official member and security leader of the famous hacktavist group Anonymous, and claims the move is a reaction to the company’s support of the U.S. government’s efforts “to censor and control the Internet,” through its support of the Stop Online Privacy Act (SOPA).
GoDaddy is currently the largest domain registrant in the world, and is four times the size of its nearest competitor. GoDaddy reportedly manages more than 48 million domain names and serves more than 9.3 million customers. The outage affected not only those sites hosted by GoDaddy, but also those registered with the company which includes thousands of websites, big and small. Reports also show the FBI and DOJ, the Recording Industry of America, Motion  Picture Association of America, Universal Music and BMI.com websites were also attacked by this movement. The hacking group is trying to claim retribution for anti-piracy efforts by both the government and the entertainment industry. Picture Association of America, Universal Music and BMI.com websites were also attacked by this movement. The hacking group is trying to claim retribution for anti-piracy efforts by both the government and the entertainment industry.
Who is Anonymous you might ask…..
Anonymous is a loosely associated hacktivist group. It originated in 2003 on the website 4chan.com, an image sharing website where a large number of online community users simultaneously exist as a “digitized global brain”. It is also generally considered a term used for members of certain Internet subcultures, where their actual identities are not known. In its early phase, the concept had been adopted by a spread out online community acting anonymously in a coordinated manner against a loosely self-agreed goal, and was primarily focused on entertainment. In 2008, they began increasingly associating with collaborative, international hacktivism. Although it’s not necessarily tied to a single online entity, many websites are strongly associated with Anonymous. This includes popular imageboards such as 4chan, their associated wikis, Encyclopedia Dramatica, and a number of other forums.
 Anonymous has claimed involvement in a number of cyber-attacks in the past including attacks against the Pentagon, News Corp, Monsanto, Visa, MasterCard, PayPal, GM, and other Government websites. They have even threatened to destroy Facebook. Their coordinated community is not only involved in cyber-attacks, it has also partly organized activist movements such as Occupy Wallstreet, and have been responsible for tracking down wanted criminals that lead police to an arrest. Anonymous has claimed involvement in a number of cyber-attacks in the past including attacks against the Pentagon, News Corp, Monsanto, Visa, MasterCard, PayPal, GM, and other Government websites. They have even threatened to destroy Facebook. Their coordinated community is not only involved in cyber-attacks, it has also partly organized activist movements such as Occupy Wallstreet, and have been responsible for tracking down wanted criminals that lead police to an arrest.
A recent statement by Anonymous read: “We will continue to attack those who embrace censorship. You will not be able to hide your ludicrous ways to control us”. So now the question is: Who will be the next target of Anonymous, and how long before we see another attack?
>> Did you like this article? Ping it!
Tags: 0wn3r, 4chan, anonymous, anonymous owner, Arizona, attacks, censor, censorship, crash, cyber attack, doj, domain names, down, fbi, go daddy, godaddy, hack, hacked, hacking, hactivist, internet, outage, responsibility, sopa, stop online privacy act, twitter, web hosting, web servers, websites
Posted in Tech Club General | No Comments »
Thursday, July 5th, 2012
 Most companies today depend on technology to survive and most people make use of a computing device at some point every single day to get the job done. In an ever more connected world, people work together using a combination of computers, tablets, and smartphones over local and global computer networks. It’s a fact that technology has changed the game for modern business, and the company with the best technology wins, allowing employees to work faster and more efficiently than competitors. Most companies today depend on technology to survive and most people make use of a computing device at some point every single day to get the job done. In an ever more connected world, people work together using a combination of computers, tablets, and smartphones over local and global computer networks. It’s a fact that technology has changed the game for modern business, and the company with the best technology wins, allowing employees to work faster and more efficiently than competitors.
What’s the best way for you, the modern business owner, to manage the critical technology for your business? There are a couple of different options. First, you can let Joe, the ‘shade tree tech’ who works in HR, handle all of the technology issues. Second, you can hire a full time Information Technology Specialist. And third, you can hire a professional outside computer consulting company to handle the technology side of your business. Let’s briefly examine the pros and cons of all three options:
Enlisting a Non-Technical Employee
| Pros: |
|
Cons: |
- This is the lowest cost solution
|
|
- Asking someone who is not technically inclined to do technical work can easily frustrate them, leading to an unhappy worker
- Problems are often resolved the wrong way, what seems like a working fix at the time eventually leads to larger and more costly problems
- Without detailed knowledge of the latest trends in the technology industry, these types of workers are unable to provide good input on hardware or software upgrades that can help your business run faster to remain competitive
- Smaller jobs may be completed quickly, such as clearing a jammed printer, but projects that exceed this workers computer experience will take five to ten times longer to resolve than the time it would take a trained professional to do the same
- They are unable to perform their main job functions while messing around with technical issues
|
Hiring a Full-Time Technology Worker
| Pros: |
|
Cons: |
- You usually receive a high level of technical support
- Your business can stay abreast of new changes in technology to help remain competitive
|
|
- This solution costs the most to sustain, since technology employees are specialized and annual wages to retain them are high
- For most small businesses under twenty employees, your technical worker will not have enough work to justify a full days salary
- Without someone already on staff with a background in technology, finding and hiring the right candidates for the job can become difficult and time consuming
- If this worker leaves unexpectedly, they can leave your business in a very tough spot
|
Hiring to a Computer Consulting Company
| Pros: |
|
Cons: |
- This solution costs significantly less than a full-time employee, for as little as $3,800 per year you can keep your technology infrastructure running smoothly
- You don’t have the overhead associated with employing or managing a full-time worker
- The level of technical support you receive is often higher than that of an in-house staff, since the computer professionals you will be dealing with often have many years of in-depth hands on experience
- A technology consultant has access to resources on his team that you don’t get with a single employee, including sophisticated tools, training materials, and additional technology specialists who can assist them with projects when necessary
- Even when employees change, your IT infrastructure is safe
- Your business remains highly competitive, as you’re dealing with IT professionals who work with dozens of businesses each year and know about all of the latest productivity enhancing hardware and software solutions available
- Their up to date training includes many of the latest mobile apps that can help mobilize your workforce via smartphones, tablets, and the cloud
|
|
- Finding a reliable company can be difficult
|
For most small to medium size offices the choice between a non-technical employee, a full-time technical employee, or a technology consulting firm should be a no-brainer. At going rates an outside IT firm can save your business $44,000 per year in operating expense vs. hiring a full-time employee. An outside IT company also provides the security of knowing that your critical IT infrastructure is safely managed by trained professionals.
What would one day of down-time going to cost you? What would one week cost? It’s not necessary for you to find out! For a minimal investment, an IT support company like my PC Techs can come into your Phoenix area office once a week or once a month and perform routine server maintenance, computer maintenance, and make sure the network and systems are running optimally. Beyond that, your expert computer technicians can provide group training on new software, help upgrade existing software to newer and faster versions, and provide consultation on how to spend technology budget in a way that provides the best bang for the buck.
Save time, save money, and increase productivity by hiring the experts at my PC Techs to maximize your uptime! Call (602) 456-0150 to schedule a free consultation today.
Tags: business, business owner, computer consultant, computer consulting, computer networks, computers, hardware, information technology, IT company, IT firm, it professionals, IT support, phoenix, smartphones, software, tablets, technical employee, technology, technology consultant, technology employees, technology industry, upgrades
Posted in Tech Club General | No Comments »
WE WORK HARD FOR YOU, BUT DON'T JUST TAKE OUR WORD FOR IT!
We've helped over 1,000 satisfied businesses throughout the Phoenix valley, click here to view some of their testimonials:

©2010 my PC Techs is owned and operated by Leo Polus, L.L.C., concept by Andre Morris |
| |





 GoDaddy, an Arizona web hosting company, experienced severe outages yesterday. The massive Distributed Denial of Service (DDoS) began late Monday morning, and the
GoDaddy, an Arizona web hosting company, experienced severe outages yesterday. The massive Distributed Denial of Service (DDoS) began late Monday morning, and the 
 Anonymous has claimed involvement in a number of cyber-attacks in the past including attacks against the Pentagon, News Corp, Monsanto, Visa, MasterCard, PayPal, GM, and other Government websites. They have even threatened to destroy Facebook. Their coordinated community is not only involved in cyber-attacks, it has also partly organized activist movements such as Occupy Wallstreet, and have been responsible for tracking down wanted criminals that lead police to an arrest.
Anonymous has claimed involvement in a number of cyber-attacks in the past including attacks against the Pentagon, News Corp, Monsanto, Visa, MasterCard, PayPal, GM, and other Government websites. They have even threatened to destroy Facebook. Their coordinated community is not only involved in cyber-attacks, it has also partly organized activist movements such as Occupy Wallstreet, and have been responsible for tracking down wanted criminals that lead police to an arrest. Most companies today depend on technology to survive and most people make use of a computing device at some point every single day to get the job done. In an ever more connected world, people work together using a combination of computers, tablets, and smartphones over local and global computer networks. It’s a fact that technology has changed the game for modern business, and the company with the best technology wins, allowing employees to work faster and more efficiently than competitors.
Most companies today depend on technology to survive and most people make use of a computing device at some point every single day to get the job done. In an ever more connected world, people work together using a combination of computers, tablets, and smartphones over local and global computer networks. It’s a fact that technology has changed the game for modern business, and the company with the best technology wins, allowing employees to work faster and more efficiently than competitors.





